
Business Email Protection: Check the “From”
One of the best telltale signs behind a phishing attempt can often be found in a sender’s email address. In order to trick people, phishing

One of the best telltale signs behind a phishing attempt can often be found in a sender’s email address. In order to trick people, phishing

This is a reminder to everyone that phishing attempts can pretend to be your bank, the ATO, PayPal, or any other organization. Phishers will often

Are you being asked for a PIN when using Microsoft’s Authenticator app? Microsoft Authenticator now has “App Lock” enabled by default and you can see

Do you need to integrate your partner’s Gmail calendar to your Outlook work calendar so you can see each others appointments? Would you like to
The problem was caused by an Excel file which reached its maximum size during an automated transfer process. Although Excel is widely used, experts say

What is Shadow IT? As businesses move towards the cloud, it is important to know how your employees are utilizing cloud services. Employees signing up

Even though we now offer web design, our service doesn’t suit everyone. We’ve seen a few customers sign website contracts for websites that have given

Not all hosting providers will provide the same quality of service for your website. A good hosting provider will be proactive in maintaining and securing

It’s big news when one of the largest organisations in the world offering IT certifications and security training gets hacked and this is what happened
Walkie Talkie is a new feature coming soon to Microsoft Teams. If you have a headset device with a “press to talk” button, you can

Watch this one come around to bite people in a few months. Pretty much every server needs to be patched. The EXTERNAL risk might be
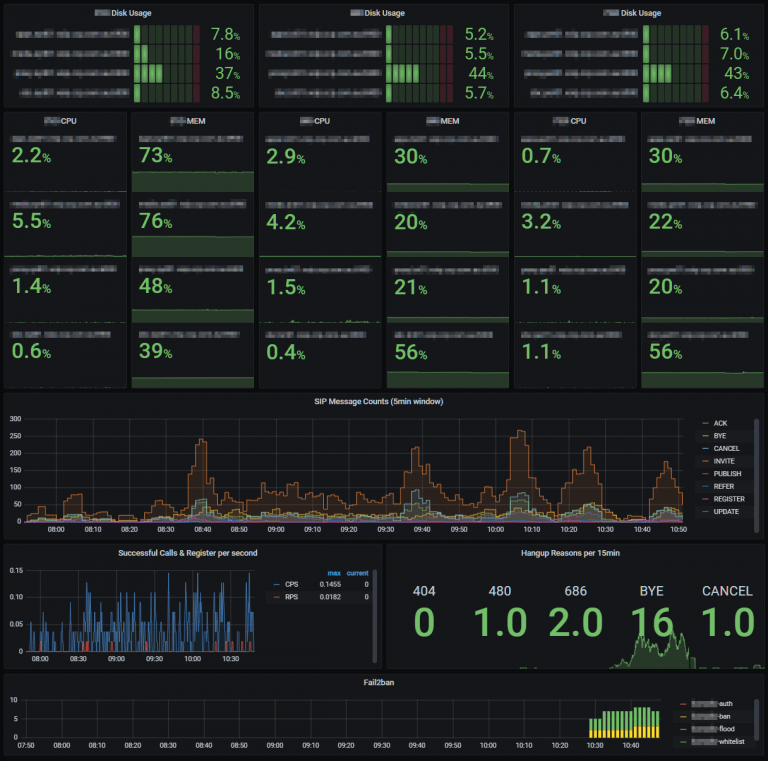
Monitoring data is vital in making sure systems are running as they should be. Without proper monitoring, problems can go unseen and lead to ongoing