There is an increasing amount of Phishing attacks targeting services such as Office 365, Gmail, Dropbox and other services. These attacks are launched from compromised accounts that you may trust and constructed in a way to piggyback off an existing conversation to increase the likelihood of success. Lets take a look at the anatomy of a recent attack.
Phishing Attack Setup
In this case, the attack originated from a compromised account, Dino a high level exec from Company A that has current dealings with the victims company (Company B). The attacker read Dinos mail and identified potential targets, based off existing email conversations. Anything that involved sending documents, proposals or dealt with financial information, such as invoicing, accounts or payroll.
One victim will be a mid-level employee, Jack, at Company B, who is expecting a PDF proposal from Dino.
The Delivery
The attacker identified an email conversation between Dino and Jack, where Jack is expecting a file of some sort. He also uses the file sharing service “egnyte” and uploads a html file. He then shares the file with the Jack via egnyte, so that he receives the following email;
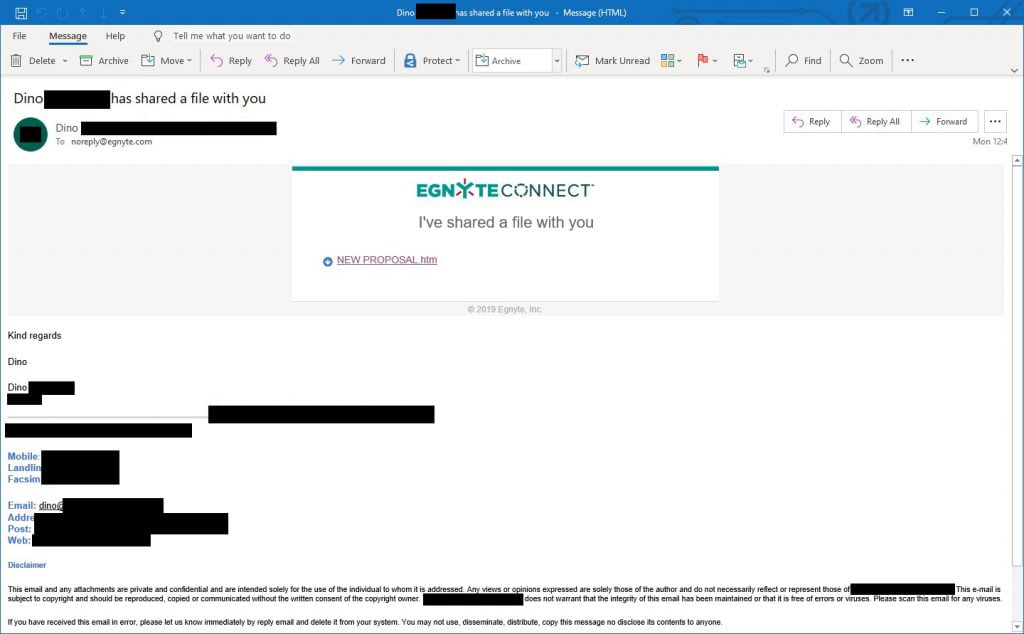
Jack has phishing protection services, safe link scanning and antivirus which are all functioning correctly. Because the email is originating from a real account (that has been compromised), it passes all the phishing checks. Because the link in the email is simply to a file sharing service that has been used before, the link itself is considered safe.
To anyone, the email looks normal, coming from someone they trust, in an existing conversation using a file service they’ve seen before. The only thing in this entire email that throws a red flag would be the file being shared, namely “NEW PROPOSAL.htm”. It is not a PDF that one would expect and who sends a proposal via a html file?
The Payload
Jack clicks the link which takes them to the valid egnyte file sharing website;
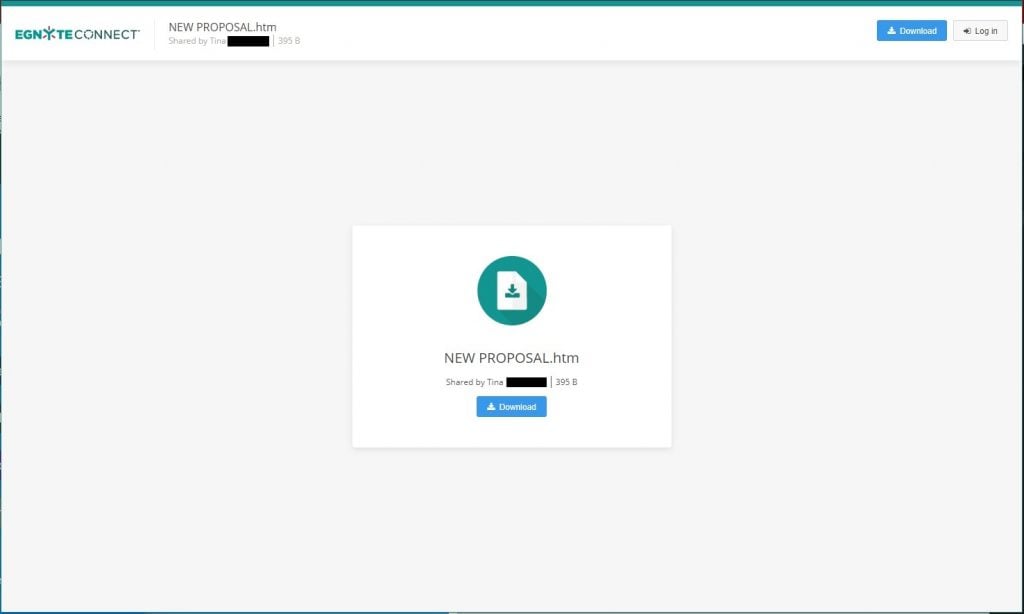
The second red flag is shown as Dino was the person apparently sharing the file but this page shows that it is being shared by Tina. A small detail easily overlooked. Jack downloads the html file to their computer and tries to open it. Because the file is a simple HTML file, like any webpage, the virus scanner detects no malicious payload. All the HTML document does is redirect the viewer to another page, where the actual phishing occurs. After running the file, the victim is presented with the following;

This is where the largest red flags are shown. As an example;
- The file has already been downloaded, why would the victim Jack now need to sign in?
- Jack has never had to sign in before to access documents from Dino
- The URL on the sign-in page is “srgilimited.com” and does not look anything like the Microsoft sign-in url
- The file was shared via egnyte, why is onedrive, a different service, asking for sign-in
- This looks nothing like the normal OneDrive sign-in page
- If you enter bogus details, it still continues and downloads a harmless pdf file
Preventing Phishing Attacks
In the example above, the Jack already had link protection, phishing protection and antivirus but the methodology employed managed to bypass those protections. In the above example, the victim managed to change their password before the attackers gained access (which we thankfully proved due to our enhanced sign-in auditing). The best protection however, is a layered defense. Enabling multi-factor authentication would have rendered this attack useless and is still the best protection against credential stealing.
However, this attack was focused on getting passwords. What if the attack replaced the payment details on an invoice, sent a message to payroll to update wage payment details or other methods which are not protected by multi-factor authentication. Therefore, we always recommend;
- Email threat protection (phishing, malware and virus Scanning)
- Anti-spoofing measures to prevent sender faking
- DNS security filtering
- Enabling multi-factor authentication
- Replacing internal communication with a messaging platform like Microsoft Teams
- Education and training for all staff
Education, the best preventative measure
Ultimately, attackers are getting better and your staff need the knowledge and tools to identify them. With a proper training program, you can test your team to see who is vulnerable and with very little training, drastically increase the chance to spot phishing attempts the first time.
You can BOOK A VISIT from one of our consultants or CONTACT US to see how our services can deliver a multi-layered defense strategy for your business.