Proofpoint, Inc., a leading cybersecurity and compliance company, released its annual Human Factor report this month. We’ve gone through it to see what key takeaways there are for accountants, lawyers and other SMBs.
Yes, you are a target
No matter how big or small, widely distributed tools are allowing threat actors to target everyone. A staggering 94% of cloud tenants are targeted every month. Of these targeted businesses, 62% were successfully attacked, with the monthly sucess rate averaging around 20%.
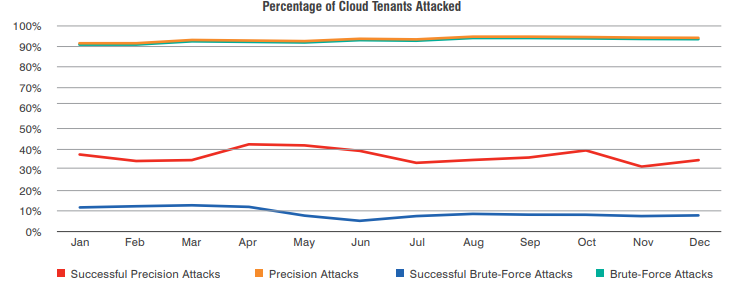
The good news is that last year, that monthly rate was around 24% which indicates system administrators may be taking extra steps to protect their systems and users.
As defence evolves, so do the attacks
Attack chains became more varied. Methods to deliver attacks were rapidly tested and discarded. Although there’s a consistent split of attacks between urls and attachment methods, we still see social engineering play the central role in most cyber attacks. The vast majority relied upon psycological manipulation.
No matter the method of attack, these threat actors are most invested into gaining access to corporate credentials and devices.
Multi-Factor Authentication can be bypassed
There’s a false sense of security being spread when Multifactor Authentication (MFA) is enabled. Users then consider their data secure and can lower their security posture. Although possible for some time (and we’ve even run proof of concepts in house), new off-the-shelf tools make MFA bypass easier than ever.
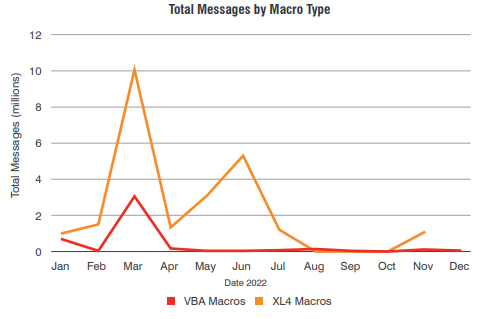
Office macro attacks go down
As microsoft has been enforcing greater security around office macros, attackers have moved on to other more viable targets.
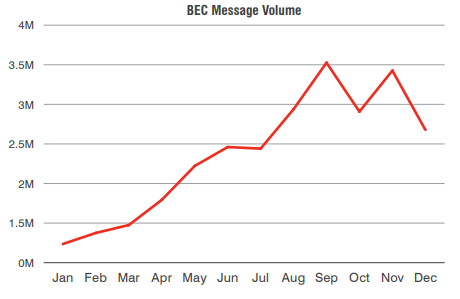
A rise in Business Email Compromise
Attacks are financially motivated and you don’t have to be the victim of a compromised account, to be a victim of financial theft. An increase was seen where threat actors would compromise an email account at one company, and leverage that access to distribute fake invoices and money transfers via normal business flows. So if you ever see a change of bank details request or an invoice that doesn’t match your purchase order, maybe give your valued vendor or customer a call to verify the details.
How do I protect my business from hackers?
You can always contact us for a free consult. As the threat landscape is constantly changing, it’s important to have a threat intelligence partner that will move with those changes and adapt rapidly. Consider enacting conditional access, cybersecurity awareness training and monitoring your environment with an external Security Operations Center.
A lot of these solutions may be more affordable than you think, and a far more desirable option than having to deal with a breach.