A Question
“Why are a lot of fake voicemail messages not getting caught by our spam filter?”
This is just one example of many. This may not resemble all attacks but has a lot of typical indicators.
I got asked this question last night. I investigated only to find that as far as a simple spam filter is concerned – They are 100% correctly formatted and sent emails. Typical protections like SPF (Sender Policy Framework) and DKIM (DomainKeys Identified Mail), designed to protect people from impersonating domains, were set up correctly and passing for the domain in question (vtlaud.com).

Suspicion
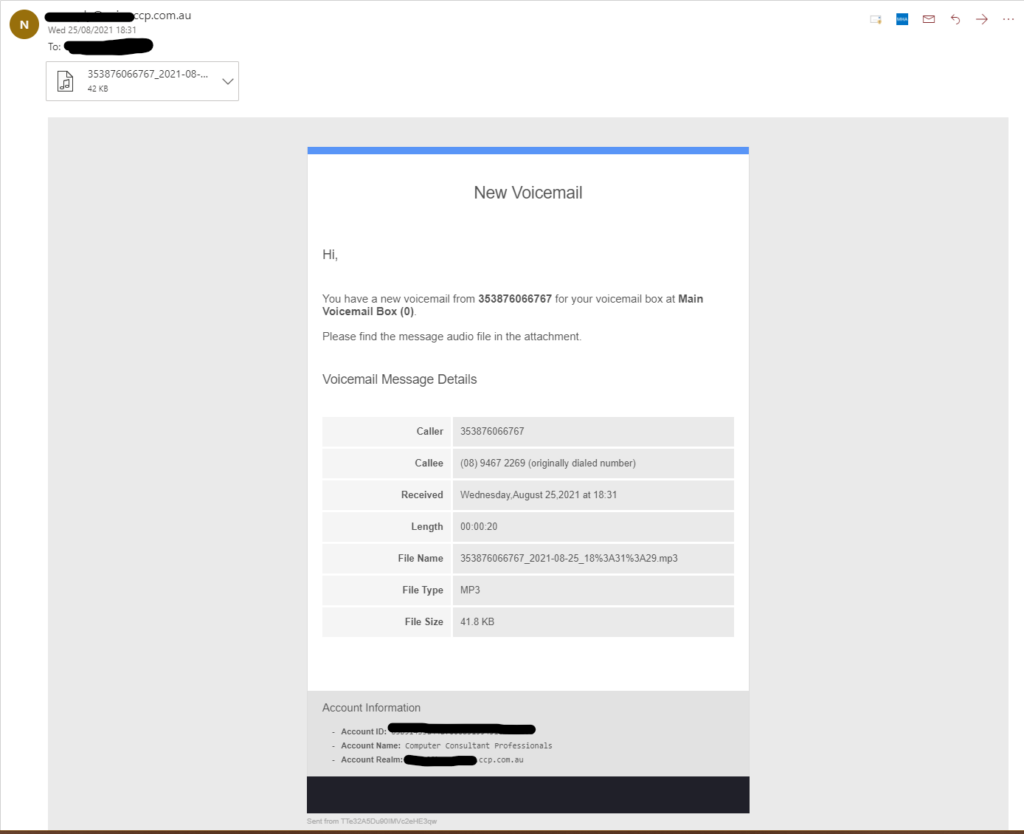
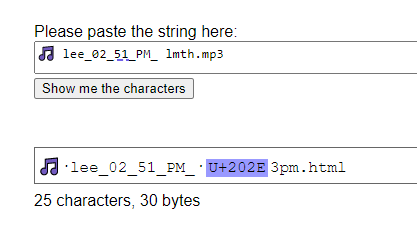
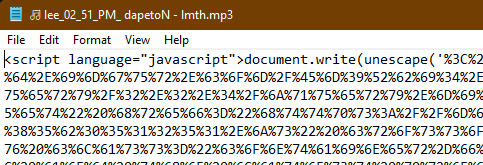
Looks legitimate but there’s a couple of giveaways. The whole message is an image (cannot select text), and there’s a suspicious looking attachment. Firstly, the music note in the file name and secondly the .mp3 extension, with the icon for the Microsoft Edge browser instead of my media player. While the music note is a valid character, there’s no benefit to including it.
Upon saving the file, Explorer confirmed the type of file as a Microsoft Edge HTML Document. Meaning that if I was to double click to open, it would open in my browser, showing me some sort of web page instead of playing any voicemail message. Interestingly enough, lmth is html backwards.
Copying and pasting this filename into a handy web tool revealed the truth. The character U+2020E is a “Right-to-Left Override”. This makes Windows display the text after it in right-to-left instead of English’s typical left-to-right reading order.

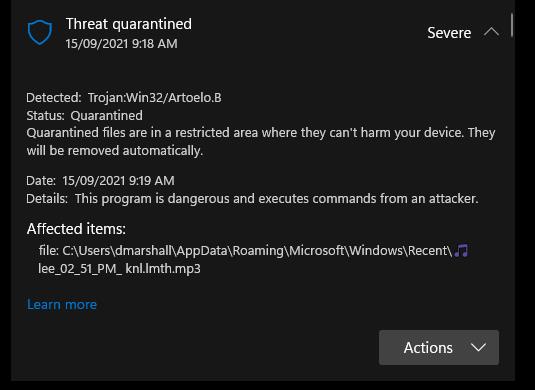
Windows Defender on Windows 11 detects the file as malicious but let’s find out what it looks like if we were to fall for the attack.
Falling For It
Opening the file in a safe environment leads to a Microsoft Login page, with an email address already helpfully pre-filled!
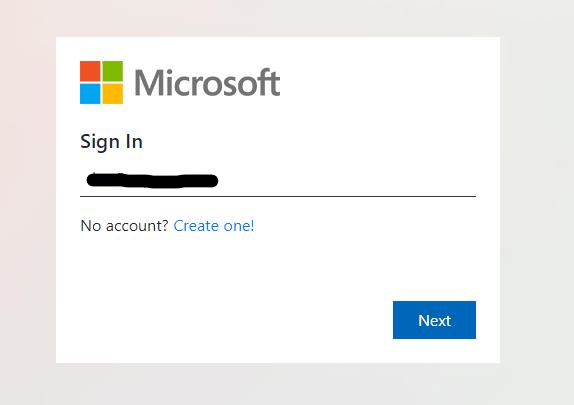
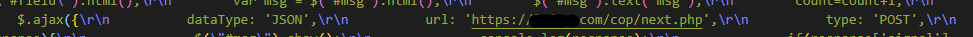
On submission of the fake login form, this page sends your data to a URL that is clearly not Microsoft. I’ve hidden the URL for safety. The DNS filtering service we provide to customers blocks this URL so anyone using our Managed IT Services with security would have had this attack prevented.
Once you’ve submitted the form, the page also redirects to a legitimate voicemail message, making you believe you successfully logged in and a caller had left you a useless and confusing message. The message doesn’t even contain a name or call-back number.
Conclusion
This kind of attack is quite common and shows how easily you can fall into a trap. Anti-Virus on its own is no longer a viable security measure as only 9/56 tested detected this file as malicious. Measures like a DNS Filter, Multi-Factor Authentication and staff security training are all a part of the arsenal. Nothing is perfect, but the more layers in your defence, the less likely you will run into trouble.
Contact us or use the form at the bottom of the page to request a call-back to discuss services we can provide to help prevent attacks like these.
Valid Example
For clients on our Phone System this is what your voicemail messages will look like when in your inbox: